Earlier today I saw an image from this tweet:
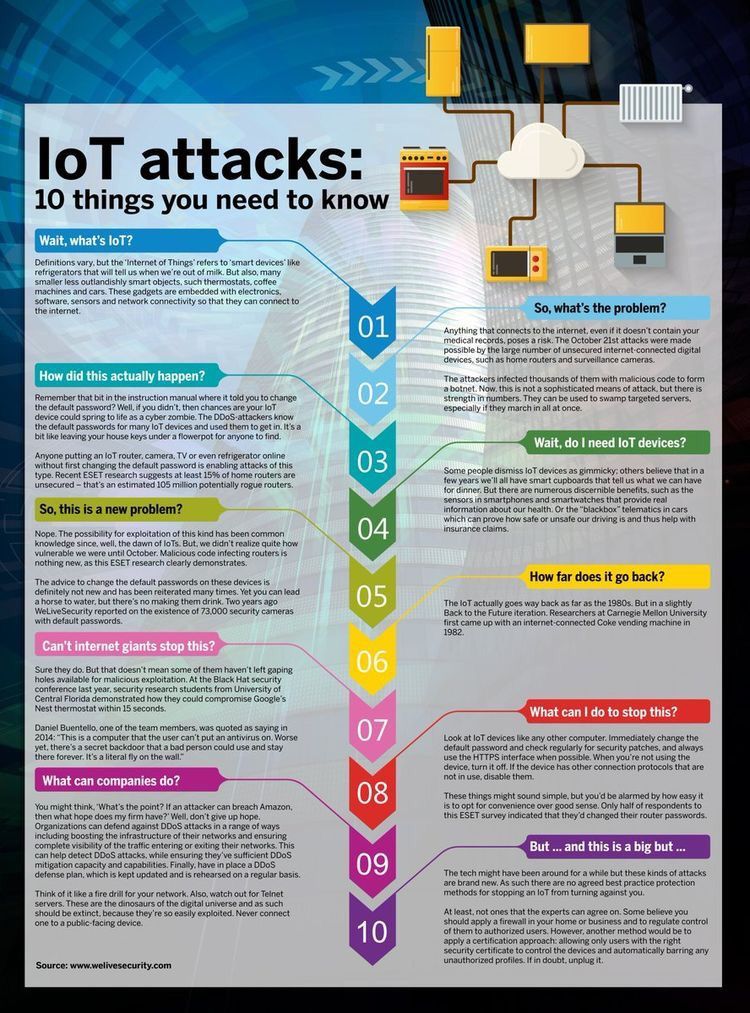
I thought I saw a few problems with it. So I decided to give the readers a more useful and correct version.
Here is where things go wrong. The tweet confuses the “Internet of Things” and routers with vulnerable firmware or services several times, which are two different things. Even worse, it mistakes “blackbox” telematics in cars as related to IoT at all, which isn’t the case. (The issue with cars is all the extra entertainment software that phones home to Mama via a handy API, or the now-computer-controlled braking and engine systems that can be reverse-engineered and controlled remotely.) Here’s a revised version. (Note that all opinions are entirely my own.)
Wait, what’s IoT?
The ‘Internet of Things’, also referred to as Cyber Physical Systems (CPS), is an extremely nebulous term. At its simplest it refers to the internetworking of unremarkable objects. Add a basic radio to a sensor, to send humidity and temperature, represented by a few 0s and 1s, and now your sensor can be part of a network. Stick that sensor inside a thermostat, give the thermostat some WiFi capabilities and a basic website, and now you can change the settings from a web browser or phone. Connect some more thermostats and give them a controller, and now you have an autonomous network in your home that can make it warmer or colder, turn on the humidifier or some fans, all without any input.
So, what’s the problem?
Where the original graphic gets it wrong is that the intent of these devices is to be accessible over a network. However, many devices are also meant to interact with smartphones, so they have Internet Protocol (IP) capabilities, to make them accessible over common Internet protocols, and often have WiFi. If your home gets wifi from a modem connected straight to the internet, and you have a wifi-connected camera, that camera can be targeted by attackers. Cameras are notorious for having default passwords or other insecure settings, and sometimes firmware problems, that can make them easy to take over. A 300,000-strong botnet called Mirai took out major websites in October of 2016 via a DDos attack. A more recent botnet called Persirai targets a thousand different models of networked (IP) cameras with the potential to take over 120,000 devices.
Now, cameras are all fine and dandy, but what if the sensor we mentioned is located in a pacemaker, sending data to a nearby internet-connected controller which passes it on to the doctor’s office? What if that controller is taken over and a person’s life is in danger?
How did this happen?
Money. It’s much cheaper (and easier) to throw together a device and sell it fast without a thought for security. By the time the combination of bad firmware, open ports and outdated software, and badly-designed websites is hacked by a researcher for Internet points, more money has likely been made than could be lost from a security incident for which the manufacturer has been held at fault. By the time a lawsuit makes its way through the courts, even more “smart” devices have been sold. Worst case, the manufacturer can always blame the user for poor password practices.
Wait, do I need IoT devices?
A lot of advertising goes into convincing people that they do. It’s pretty convenient to let people in front doors remotely, or check video cameras from your phone, or check your messages on a smart watch, or connect the selfie stick to your phone so you can take pictures remotely. On the flip side, there are numerous accounts of websites that collate data from IoT devices having their data stolen or toys that can easily be controlled remotely, and even a Twitter account (@InternetOfShit) devoted to all the absurd devices which can now be used with WiFi or the internet. (My favorite is the $150 “smart” toothbrush, complete with phone apps, to game-ify brushing teeth).
So, is this a new problem?
Anyone capable of understanding the risks of permitting thermostats or HVAC systems to connect to the internet, sometimes by force, has been warning about this for years, unheeded while the money rolled in. Once people couldn’t Netflix and chill on a Friday afternoon while idly swiping through the latest news stories, a great hue and cry arose. Every mom-and-pop security company jumped on the “I-told-you-so” bandwagon in the hopes of getting more business or clicks for advertising.
How far does the IoT go back?
The concept of giving the internet to the masses has existed since AOL starting sending out coffee-coasters in the mail. The concept of giving the internet to masses of otherwise invisible objects like trashcans in the street or the lightbulbs in the home has come about in the last 15 years.
Can’t Internet giants stop this?
It’s not just out of their hands, it’s not something they can begin to fix, unless they own the companies that manufacture vulnerable devices, such as Google’s Nest thermostat. Pretending that “internet giants” have anything to do with this indicates a deep lack of understanding of the Internet and I suggest a refresher course in Internet Protocols, or better yet the whole OSI model. Start with the bottom-most physical layer and work your way up.
What can I do to stop this?
Don’t buy Internet-enabled sex toys. But if you want to see the garden on your porch from an IP camera while you’re in a different city and climate altogether, make sure to change the default passwords, upgrade the firmware when possible, and disable unused services (usually in the settings). It doesn’t matter if you use the HTTPS interface as long as you’ve got a password on your wifi network, which nearly everyone does these days.
What can companies do?
Organizations can defend against DDoS attacks by ensuring that they have a robust and secure edge firewall solution in place. Consider using Access Control Lists to ensure incoming traffic is directed properly. Websites can use DDoS protection services such as CloudFlare to help absorb any DDoS traffic that could be directed at them.
If companies are using IP-enabled devices, consider segregating such devices in a DMZ network or on a separate VLAN entirely, as these devices should not be on the same network as production servers or end-user devices. If your organization has assumed a risk mitigation approach to security, network segregation will help when, not if, IP devices are attacked or compromised.
But … and this is a big but …
If the average site gets hit with 1.2 TB/s traffic, as was seen in the Mirai attack in October 2016, it will go down and no amount of DDoS protection is likely to help. Additionally, any holes in an external-facing network will be exploited by attackers in any way possible, and it is difficult to protect against all attack vectors.
P.S. What’s with the original’s color scheme??

